Proxifier
Proxifier is a powerful network tool that allows applications not natively supporting proxy servers to route their network connections through HTTP, HTTPS, SOCKS v4, v4A, and v5 proxies. It's essential for enhancing privacy, bypassing firewalls, or accessing geo-restricted content.
About Proxifier
Proxifier serves as a crucial bridge for applications that lack built-in proxy support. It acts as a layer between your network applications and the internet, intercepting network connections and redirecting them through your specified proxy server. This capability is incredibly versatile, catering to a wide range of user needs, from individual privacy enhancement to organizational network management.
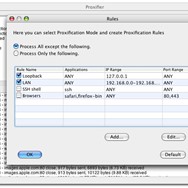
Key functionalities include granular control over which applications use which proxies through customizable rules. These rules can be defined based on application names, IP addresses, port numbers, and even target hostnames. This level of control ensures that you can precisely manage your network traffic flow.
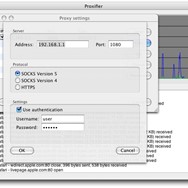
Proxifier supports a comprehensive array of proxy protocols, including:
- HTTP and HTTPS proxies
- SOCKS v4, v4A, and v5 proxies
- SSH tunnels
The software can also handle proxy chains, allowing you to route your traffic through multiple proxies sequentially for enhanced security and anonymity. Its portability feature means it can be run without installation on some systems, making it a convenient tool for mobile or temporary use.
For advanced users and scripting scenarios, Proxifier offers a command-line interface, enabling automated configuration and task execution. This is particularly useful in professional environments or for integration with other tools.
Overall, Proxifier provides a robust and flexible solution for managing network connections through proxies, making it an indispensable tool for anyone needing to route applications through proxy servers effectively.
Pros & Cons
Pros
- Forces any application to use a proxy.
- Highly customizable rule-based configuration.
- Supports a wide range of proxy protocols (HTTP, HTTPS, SOCKS, SSH).
- Allows for proxy chaining and DNS proxying.
- Includes a portable version for flexible use.
- Features a command-line interface for automation.
Cons
- Can potentially introduce some network latency.
- Requires basic understanding of proxy concepts for optimal configuration.
- The interface, while functional, might appear dated to some users.
What Makes Proxifier Stand Out
Force Proxy Usage
Enables any application, regardless of its native support, to use proxy servers for network connectivity.
Granular Rule Control
Provides precise control over which applications use which proxies and under what conditions.
Comprehensive Protocol Support
Compatibility with multiple mainstream proxy protocols, offering flexibility in connection types.
Features & Capabilities
11 featuresExpert Review
Proxifier: A Comprehensive Review
Proxifier is a specialized software designed to address a common challenge in networking: getting applications that lack built-in proxy support to utilize proxy servers. This capability is invaluable for a variety of reasons, including enhancing online privacy, bypassing geographical restrictions on content, and navigating network firewalls. This review examines the functionality, usability, and overall effectiveness of Proxifier.
Core Functionality and Protocol Support
At its core, Proxifier intercepts network connections made by specified applications and redirects them through configured proxy servers. This is achieved through a low-level mechanism that essentially 'forces' applications to use the defined proxy routes. The software boasts support for a broad spectrum of proxy protocols, including HTTP, HTTPS, SOCKS version 4 and 5, and importantly, SSH tunnels. This extensive protocol support is a significant advantage, providing users with flexibility in choosing the most suitable connection type for their needs.
Rule-Based Configuration: Precision and Control
One of Proxifier's most powerful features is its rule-based configuration system. Users can create highly specific rules that dictate which applications, targeting which IP addresses, hostnames, or port numbers, should use a particular proxy or be excluded from proxying. This level of granularity is exceptional and allows for fine-tuned control over network traffic. For example, a user could configure Proxifier to route only web browser traffic through a proxy while allowing other applications direct internet access, or vice-versa. This rule system is intuitive to configure through the graphical interface, using include and exclude lists, and offers a high degree of customization.
Advanced Features: Chaining and DNS Handling
Beyond basic proxying, Proxifier offers advanced features that enhance its utility. The ability to chain proxies allows users to route traffic through multiple proxy servers sequentially. This can significantly increase anonymity and security by obscuring the origin of the network connection through multiple hops. Furthermore, Proxifier can be configured to route DNS requests through the proxy server. This is a critical feature for privacy, as it prevents potential DNS leaks that could reveal the user's actual location or browsing activity even when using a proxy.
Usability and Interface
The user interface of Proxifier is functional and well-organized. The main window provides a clear overview of active network connections and the rules being applied. Configuring proxies and rules is straightforward through dedicated menus and dialogs. While the initial setup might require some understanding of proxy concepts, the interface is not overly complex. The software runs in the background, with minimal intrusion on system resources once configured.
Portability and Command-Line Interface
Proxifier also offers portability, meaning it can be run from a removable drive without requiring a full installation on the host system. This is advantageous for users who need to apply proxy settings temporarily or on multiple machines without leaving a software footprint. For system administrators and advanced users, the inclusion of a command-line interface is a significant plus. This allows for scripting and automation of Proxifier configurations, making it easier to integrate into larger network management systems or to perform repetitive tasks.
Performance Considerations
As with any proxying solution, there can be a potential impact on network performance. Routing traffic through one or more proxy servers naturally adds latency. However, Proxifier is designed to be as efficient as possible. The degree of performance impact will heavily depend on the speed and reliability of the proxy servers being used and the number of chained proxies. For most general use cases, the performance overhead is often negligible.
Conclusion
Proxifier is a robust and highly capable software for managing network connections through proxies. Its ability to force any application to use a proxy, coupled with its granular rule-based system, extensive protocol support, and advanced features like proxy chaining and DNS handling, makes it a powerful tool for both individual users and organizations. While some basic understanding of networking and proxies is beneficial for optimal configuration, the interface is user-friendly enough for most users to get started. For anyone needing to effectively and flexibly route application traffic through proxy servers, Proxifier stands out as a leading solution.